“Technology is the engine of healthcare — and today, that engine runs on the cloud,” says Adam, host of HIPAA Insider, kicking off a discussion that every healthcare organization needs to hear. “But with great power comes, as always, great responsibility.”
In this episode of HIPAA Insider Podcast, Adam and Gil Vidals, CEO of HIPAA Vault, unpack the top 10 HIPAA cloud compliance FAQs that healthcare IT teams ask every week.
From shared responsibility to encryption, backups, and the myth of “automatic compliance,” this guide simplifies the technical details — so you can confidently secure protected health information (PHI) in the cloud.
1. If I sign a BAA with AWS, Azure, or Google Cloud, am I automatically HIPAA compliant?
“That’s a big misconception,” explains Gil. “Just because a cloud provider offers a Business Associate Agreement (BAA) doesn’t mean your environment is HIPAA compliant out of the box.”
Major cloud providers such as AWS, Azure, and Google Cloud offer HIPAA-eligible services, but you — the customer — must configure those services correctly to ensure compliance.
Each cloud provider maintains a list of HIPAA-eligible tools, but security features like encryption, identity management, and audit logging must be enabled and maintained.
Tip: Partner with a managed HIPAA cloud provider like HIPAA Vault that handles configuration and compliance monitoring for you.
→Request a Consultation with a HIPAA Vault expert
Don’t Trust Patient Data to Standard Web Hosting
Protect your practice from breaches and fines. Our hosting includes intrusion detection, firewalls, and audit logs.
Learn More2. What is the shared responsibility model?
“Think of it in layers,” Gil says. “The big cloud providers handle the physical infrastructure — the buildings, access controls, and hardware. You’re responsible for what runs inside.”
In short:
- Cloud provider: Handles physical security and infrastructure uptime.
- Customer (you): Handles data security, configurations, access control, and application compliance.
For example, enabling encryption or setting user permissions for your web app is part of your responsibility under HIPAA.
→ Learn more about HIPAA-compliant hosting solutions designed to simplify this shared model.
3. Is hosting ePHI in the cloud more secure than local servers?
“Ten years ago, people loved their server closets,” Gil recalls. “They thought having servers next to their desk was safer. But that was never really true.”
Cloud providers invest billions in advanced security — physical access controls, redundant power, and 24/7 monitoring — that few organizations can match.
Local servers, on the other hand, are vulnerable to theft, outdated hardware, and limited physical security.
Conclusion: Properly configured HIPAA cloud hosting is far more secure than most on-premise setups.
4. Is encryption mandatory for HIPAA cloud compliance?
Yes — effectively, it is.
While HIPAA lists encryption as an addressable safeguard, it’s considered essential for electronic protected health information (ePHI). You need:
- Encryption in transit (via TLS)
- Encryption at rest (via AES-256 or equivalent)
“If a breach occurs and your data was encrypted,” notes Gil, “HHS says that information is unusable, unreadable, or indecipherable — meaning you may not have to report it under the Breach Notification Rule.” (Source: HHS.gov)
→ HIPAA Vault encrypts both in-transit and at-rest data as part of our managed HIPAA cloud services.
Managed Enterprise Hosting on Google Cloud Platform
Leverage the power of Google Cloud with guaranteed compliance. We manage Kubernetes, APIs, and databases for high-scale healthcare apps.
Learn More5. Does ePHI have to stay in U.S.-based servers?
Technically, HIPAA doesn’t forbid storing ePHI overseas — but HHS strongly discourages it.
“If your data sits in another country,” Gil explains, “you lose legal jurisdiction. If an employee overseas mishandles data, you can’t easily take action.”
Unless your organization has global legal infrastructure, keep your ePHI in U.S. data centers where HIPAA enforcement applies.
6. Can companies really be ‘HIPAA certified’?
“There’s no government-issued HIPAA certification,” clarifies Gil. “But there are reputable third-party assessments like HITRUST or Compliancy Group.”
While these commercial certifications can improve your security posture, remember: they’re not official designations from HHS. HIPAA compliance is an ongoing process, not a one-time certification.
→ Explore HIPAA compliance risk assessments to identify and fix vulnerabilities.
7. What’s the most common cause of a HIPAA cloud breach?
Misconfiguration.
“Either someone misconfigures a firewall or leaves default settings enabled,” says Gil. “That’s where things go wrong.”
Other leading causes include:
- Poor identity and access management
- Granting excessive permissions (“keys to the kingdom”)
- Unpatched vulnerabilities
A secure cloud doesn’t protect you from human error — which is why automated monitoring and HIPAA penetration testing are essential.
🧪 See how HIPAA Pen Testing helps prevent configuration errors before they cause a breach.
8. If we use a third-party app hosted in our cloud, do we need a BAA with them?
Yes — if the third-party app handles or transmits ePHI, even indirectly, you need a Business Associate Agreement (BAA).
“Anytime you allow another party to process data — even through a plugin or integration — you must hold them accountable under HIPAA,” Gil emphasizes.
The BAA formalizes their responsibility to safeguard PHI and comply with HIPAA rules.
9. What’s one technical control we should prioritize first?
“Enable multi-factor authentication,” Gil says immediately. “It’s simple, effective, and often ignored.”
MFA adds a second layer of security — a code or token sent via SMS or an app — that stops most unauthorized access attempts cold.
🔑 The best MFA tools use time-based one-time passwords (TOTP) like Google Authenticator or Microsoft Authenticator.
💬 “Even if it seems like an extra step for users,” Gil notes, “it’s standard practice now — from banks to the Social Security Administration.”
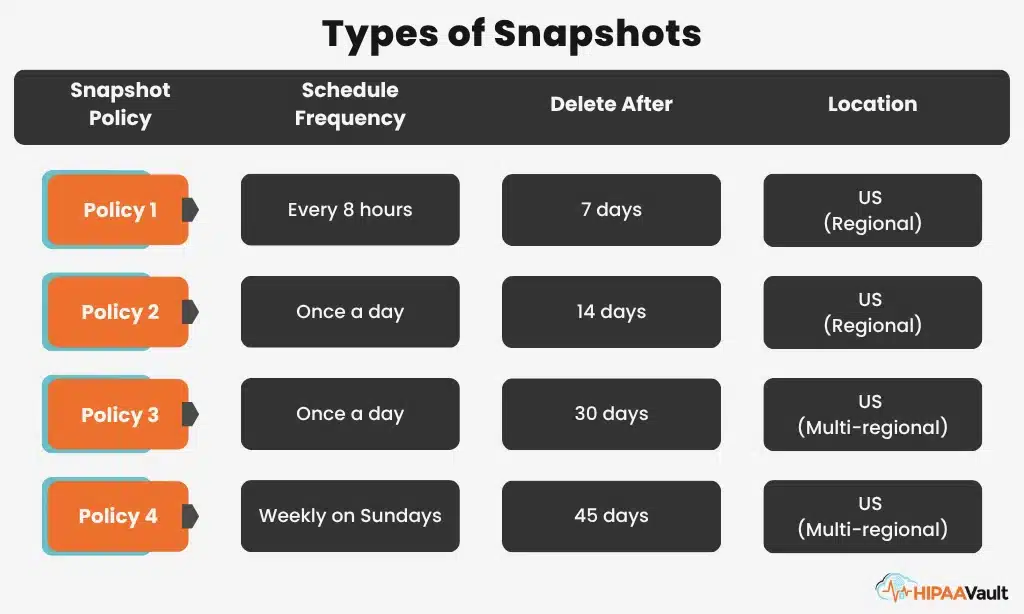
10. Do our old backup and recovery plans still work in the cloud?
Yes — but they need updating.
Cloud platforms use snapshots and automated backup utilities that you must configure.
“If you don’t enable your snapshot policy,” warns Gil, “you don’t have backups.”
Snapshots provide crash-consistent images of your data, but they’re not the same as full backups. The best approach: use both.
- Snapshots for quick recovery
- Regular backups for long-term integrity
→ HIPAA Vault’s HIPAA cloud hosting includes daily encrypted backups stored in redundant U.S. data centers.
Key Takeaway
The cloud provides incredible flexibility and scalability for healthcare — but compliance is shared. Cloud providers secure the infrastructure; you (or your managed HIPAA host) must secure the configuration, data, and access.
“The message is clear,” Adam concludes. “The cloud gives us the power, but the responsibility to configure it securely is ours.”
Next Steps for Your Organization
Trusted by healthcare providers nationwide. 100% U.S. data residency. 24/7 managed support.