For many healthcare organizations, the term “HIPAA risk assessment” is surrounded by confusion. Is it a scan? A checklist? A technical audit? A paperwork exercise?
The reality is this: a HIPAA risk analysis is the backbone of your entire compliance strategy. Without it, vulnerabilities go undetected, PHI stays at risk, and the likelihood of an OCR fine increases dramatically.
Below, we break down the four most important questions healthcare organizations ask — in clear, actionable language.
Protect Your PHI Before a Breach Happens
→ Schedule a FREE HIPAA Risk Assessment
24/7 U.S.-based support. Trusted by healthcare providers nationwide.
1. What tools are recommended for conducting a HIPAA risk assessment — and are they enough for compliance?
Many organizations believe software can “do” the risk assessment for them.
That’s one of the most costly misconceptions in HIPAA compliance.
HHS SRA Tool — Helpful, But Not Sufficient
The HHS Security Risk Assessment (SRA) Tool is free and widely used by smaller practices.
But HHS states clearly:
“The SRA tool is not a guarantee of HIPAA compliance.”
—HHS SRA Tool User Guide
Why tools alone aren’t compliant
Most tools:
- Can’t detect misconfigured firewalls
- Can’t confirm encryption
- Can’t analyze Business Associate risks
- Can’t check device/media disposal
- Can’t audit policies or training programs
- Can’t create a remediation plan
Software identifies issues — it does NOT make you compliant.
HIPAA Vault’s Recommended Approach
Use tools to gather data, but rely on compliance experts to interpret it, validate risks, and fix vulnerabilities.
→ Need help closing technical gaps?
Try our managed hosting solutions:
HIPAA Hosting Solutions
Get an OCR-Ready Security Risk Analysis
You’ll receive:
- Full SRA & gap analysis
- Remediation plan
- Policy & technical recommendations
- BAA coverage
- 24/7 support
2. Security vs. Privacy vs. Breach: What’s the difference?
HIPAA requires three different types of assessments. Understanding the differences is essential.
A. HIPAA Security Risk Assessment
The SRA evaluates risks to electronic PHI (ePHI) including:
- Access controls
- MFA
- Encryption
- Logging & audit trails
- Server/cloud configuration
- Backup & disaster recovery
- Patch management
- Network security
→ Secure your infrastructure with: HIPAA Cloud Hosting
B. HIPAA Privacy Risk Assessment
This evaluates human and workflow risks related to:
- Oral PHI exposure
- Paper records
- Minimum necessary access
- Privacy notices
- Employee training
- Improper workstation placement
- Disposal/shredding
- BAA management
Many privacy risks happen outside your servers.
C. HIPAA Breach Risk Assessment
Required under 45 CFR §164.402, this determines whether an impermissible disclosure is a reportable breach.
You must assess:
- Nature/extent of PHI
- Unauthorized person involved
- Whether PHI was viewed/acquired
- Mitigation executed
If skipped: every incident becomes a reportable breach — a costly mistake.
Stop Breaches Before They Start
HIPAA Vault helps secure your PHI with:
- Encryption at rest & in transit
- Hardened servers
- Logging & monitoring
- Daily backups
- Active intrusion protection
- Full BAA coverage
→ Get a HIPAA Hosting Quote
Fast onboarding. No long-term contracts.
3. What are the key steps in conducting a HIPAA risk assessment?
According to NIST 800-30, a HIPAA risk analysis follows a structured workflow:
1. Locate PHI/ePHI
Identify all places where PHI/ePHI is created, stored, accessed, or transmitted.
Include: servers, cloud services, SaaS apps, endpoints (laptops, tablets, phones), and backups.
2. Map PHI Flows
Document how PHI enters, moves through, and leaves your organization.
Include internal workflows, external transmissions, and vendor interactions.
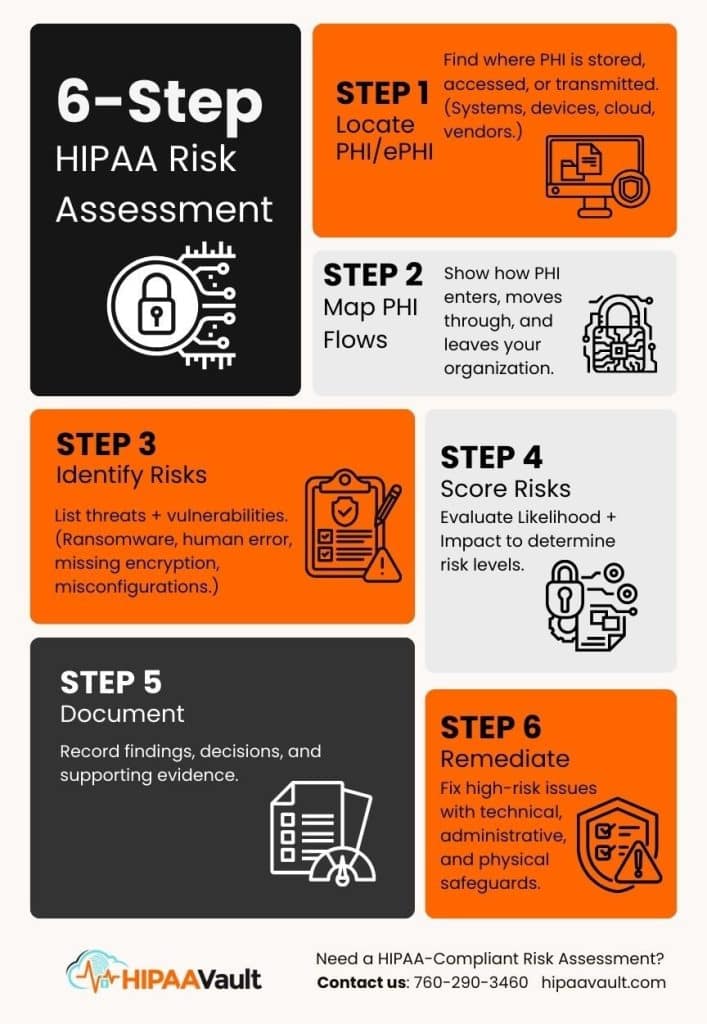
3. Identify Threats & Vulnerabilities
List all potential threats (e.g., ransomware, phishing, insider misuse, lost devices, facility issues).
Then identify vulnerabilities such as unpatched systems, weak passwords, missing MFA, outdated OS, and misconfigurations.
4. Score Risks (Likelihood + Impact)
Evaluate:
- Likelihood using NIST’s Low / Medium / High scale
- Impact across operational, financial, reputational, and patient-safety consequences
Combine these to assign final risk levels.
5. Document Findings
OCR requires written, auditable documentation.
Record: assets, threats, vulnerabilities, likelihood, impact, and assigned risk levels.
6. Create & Execute a Remediation Plan
Develop a prioritized plan to address high-risk issues using:
- Technical safeguards
- Administrative safeguards
- Physical safeguards
Focus on actionable remediation, not just discovery.
Want a Complete, Done-For-You HIPAA Security Risk Analysis?
We’ll help you:
- Identify risks
- Fix vulnerabilities
- Document controls
- Prepare for OCR scrutiny
→ Schedule Your Free HIPAA Risk Assessment
4. Why must organizations monitor Business Associate (BA) compliance?
Because you are legally accountable for your vendors.
If a billing company, cloud provider, MSP, or EHR vendor mishandles PHI, OCR can investigate you for failure to monitor your BAs.
HIPAA requires you to:
- Maintain signed, updated BAAs
- Verify BA compliance with the Security Rule
- Ensure subcontractors also follow HIPAA
- Document your oversight
- Act quickly when BA incidents occur
Most large breaches begin with a BA failure — and many organizations don’t realize they are ultimately responsible.
→ HIPAA Vault signs BAAs and provides full compliance support:
HIPAA Hosting Solutions
Eliminate Vendor Risk With a Fully Managed HIPAA Environment
- BAAs included
- 24/7 monitoring
- Managed patching & updates
- Secure configurations
- Built for covered entities & BAs
→ Contact Us for a Free Consultation
FAQs: HIPAA Risk Assessments (Expert Answers)
1. What is required in a HIPAA risk assessment?
A HIPAA risk assessment must include:
- An inventory of all systems storing or transmitting PHI/ePHI
- Identification of threats and vulnerabilities
- Likelihood and impact scoring
- Evaluation of existing security controls
- Documentation of findings
- A remediation plan with timelines
This requirement comes directly from 45 CFR 164.308(a)(1)(ii)(A).
If you need help completing these steps, HIPAA Vault provides fully managed assessments:
→ Schedule a Free HIPAA Risk Assessment
2. How often must a HIPAA risk assessment be performed?
HIPAA requires risk assessments to be performed:
- At least once every year, and
- Whenever major changes occur, including:
- New software or EHR
- Moving to the cloud
- Adding new vendors
- Network or infrastructure changes
- Mergers, acquisitions, or expansions
- New software or EHR
Annual and event-driven assessments help demonstrate “reasonable and appropriate” compliance during OCR audits.
3. Does the HHS SRA Tool satisfy HIPAA requirements?
No.
HHS explicitly states the SRA Tool:
“is not a guarantee of HIPAA compliance.”
The tool helps organizations identify risks — but it does not:
- Validate configurations
- Score risks
- Provide remediation
- Assess vendor compliance
- Replace technical testing
- Evaluate workforce policies
Most organizations use it as a starting point but rely on experts to complete the full analysis.
4. What is the difference between a HIPAA security risk assessment and a HIPAA privacy risk assessment?
A HIPAA Security Risk Assessment evaluates risks to electronic PHI (ePHI) across networks, devices, servers, access controls, and technical safeguards.
A HIPAA Privacy Risk Assessment evaluates people, workflows, and policies, including oral disclosures, printed PHI, access rights, and workforce behavior.
Both are necessary for full HIPAA compliance.
→ Secure your environment with:
HIPAA Cloud Hosting
5. What triggers a HIPAA breach risk assessment?
A breach risk assessment is triggered whenever PHI is:
- Impermissibly accessed
- Improperly disclosed
- Sent to the wrong recipient
- Appears exposed (e.g., lost device)
- Involved in a cyber incident
This assessment determines whether an event qualifies as a notifiable breach under the HIPAA Breach Notification Rule.
6. Do business associates need to perform their own HIPAA risk assessments?
Yes — every business associate must perform a HIPAA Security Risk Assessment and comply with the HIPAA Security Rule.
Covered entities must also monitor their vendors by:
- Keeping signed BAAs
- Evaluating BA compliance
- Ensuring subcontractors follow HIPAA
- Responding to BA incidents promptly
Vendor failures cause a large portion of breaches, which is why BA oversight is mandatory.
7. Does HIPAA require penetration testing?
HIPAA does not explicitly require penetration testing, but OCR considers it a “reasonable and appropriate” safeguard — especially for organizations handling high-risk ePHI environments.
→ Learn more:
HIPAA Pen Testing
8. Who should perform a HIPAA risk assessment?
HIPAA allows internal teams to conduct the assessment, but OCR strongly encourages using trained professionals due to the technical and policy complexity involved. Most organizations choose a qualified partner to ensure accuracy, documentation, and remediation support.
HIPAA Vault provides fully managed, OCR-ready assessments:
→ Request a Free Consultation
9. What happens if you don’t conduct a HIPAA risk assessment?
Failure to perform a proper risk assessment is one of the most commonly penalized violations. Consequences may include:
- Financial penalties
- Mandatory corrective action plans
- Loss of patient trust
- Breach exposure
- OCR investigations
- Reputational damage
Some fines have exceeded $1 million, even without an actual breach, simply due to “willful neglect” and missing risk assessments.
10. How long does a HIPAA risk assessment take?
Timing depends on the size and complexity of the environment:
- Small practices: 1–2 weeks
- Medium organizations: 2–4 weeks
- Enterprise systems: 4–8+ weeks
Managed providers like HIPAA Vault accelerate the process with automation, onboarding templates, and dedicated compliance engineers.
HIPAA Penetration Testing—Go Beyond Automated Scans
Validate your security with an objective, third-party audit. We simulate real cyberattacks to uncover vulnerabilities and provide a comprehensive compliance report.
Learn MoreDon’t Let Compliance Be a Guessing Game
A HIPAA risk assessment isn’t just a regulatory requirement — it’s a roadmap for protecting your organization from cyber threats, operational disruption, and costly fines.
If the process feels overwhelming, you’re not alone.
Most healthcare organizations depend on expert partners to complete a compliant SRA, implement controls, and maintain security year-round.
→ Schedule Your Free HIPAA Risk Assessment
We make HIPAA compliance simple, secure, and affordable.








