Millions of people wake up every morning, turn off their alarms, and immediately check social media, emails, or any application on their mobile devices. This has grown to be a regular routine for many.
A growing number of hackers are taking advantage of these multitudes – most of whom are still half asleep – by waging a type of social engineering attack called phishing.
Phishing comes primarily in the form of false email invitations, or emails that ask for personal login information or credentials. The goal behind phishing is to steal your personal data and information.
The emails are usually labeled as an “urgent matter” that needs to be resolved quickly, lest a penalty is incurred. The phisher sends an email that is structured to look legitimate, as if sent from an executive of a company or another trusted source.
Individuals may be tricked into believing the details of the phishing email and proceed with the given instructions. The written instructions of the email may consist of a hyperlink telling the individual to click the link and provide personal information, generally asking for usernames and passwords.
Upon clicking the hyperlink, an individual is led to a malicious website and is exposed to potentially harmful software. The hyperlink may also lead the individual to a legitimate-looking website, created by the hacker in an attempt to steal personal data or information.
Here is an example of a phishing email sent by a hacker:
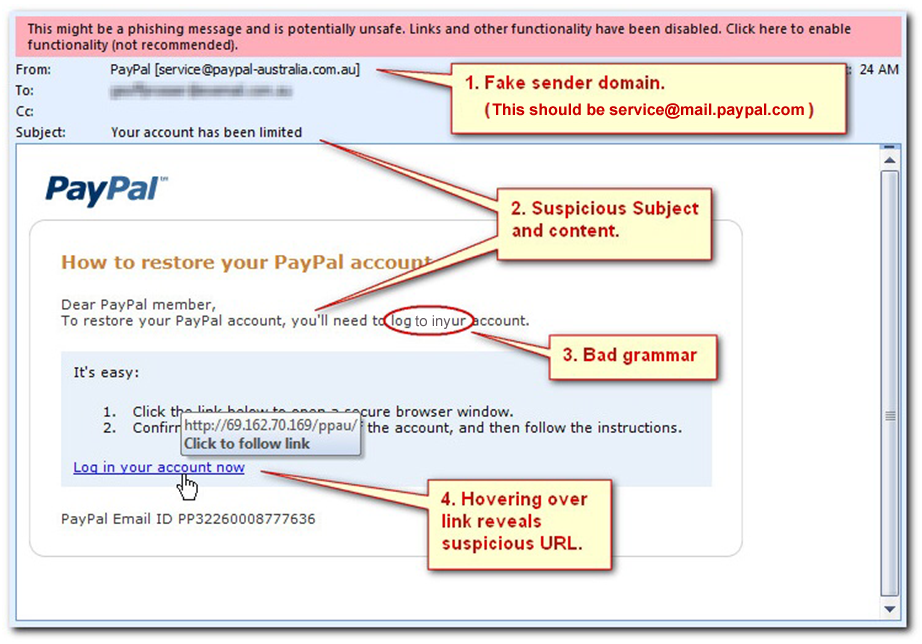
Here are four things that need to be examined:
- In the picture shown above, the email was from a fake PayPal sender. Always check the “From:” field, or the sender’s email address. The phisher may try to use a fake sender domain that resembles a real sender domain to create confusion.
- Check the subject content and the salutation in the letter. The picture above shows an example of suspicious subject matter and salutation. The salutation was generic and was not directed toward a specific person, which is a red flag. A legitimate company would greet the user with the actual first and last name of the user or with a business ID.
- Check for any grammatical or spelling errors in the writing. Number 3 in the photo shows a small grammatical error. With large and professional companies, like PayPal, the chances of an email being distributed to its members with a grammatical error is zero to none. Emails are read over by a staff of editors to ensure there are no spelling or grammatical errors.
- Run your mouse over the hyperlink if there was any provided. Hovering over a link with your mouse pointer reveals the real URL destination and can provide insight on whether the link looks suspicious. Users may not think twice when clicking a hyperlink that seems like a URL to a secure site, and end up clicking a hyperlink that leads to a fraudulent site.
If you have come across an email that may be a scam, you can report it to the Federal Trade Commission
Be sure to move the email to the trash or mark it as spam. Inform other employees and your leadership about the email, so they know not to open it.




