Electronic Data Interchange (EDI) has revolutionized the way healthcare organizations share clinical and administrative data. Under the HIPAA EDI Rule, covered entities and business associates must adhere to national standards for electronic transactions—ranging from claims submissions to eligibility inquiries—to protect patient privacy and improve operational efficiency. In this post, we’ll explore how EDI works in healthcare, key transaction sets, and best practices for maintaining HIPAA compliance.
What Is EDI in Healthcare?
EDI in healthcare refers to the electronic transfer of structured data between trading partners—such as providers, payers, and clearinghouses—using standardized transaction formats. Unlike manual processes (fax or mail), EDI automates data exchange to reduce errors, lower administrative costs, and accelerate reimbursement cycles (hipaajournal.com, clarity-ventures.com).
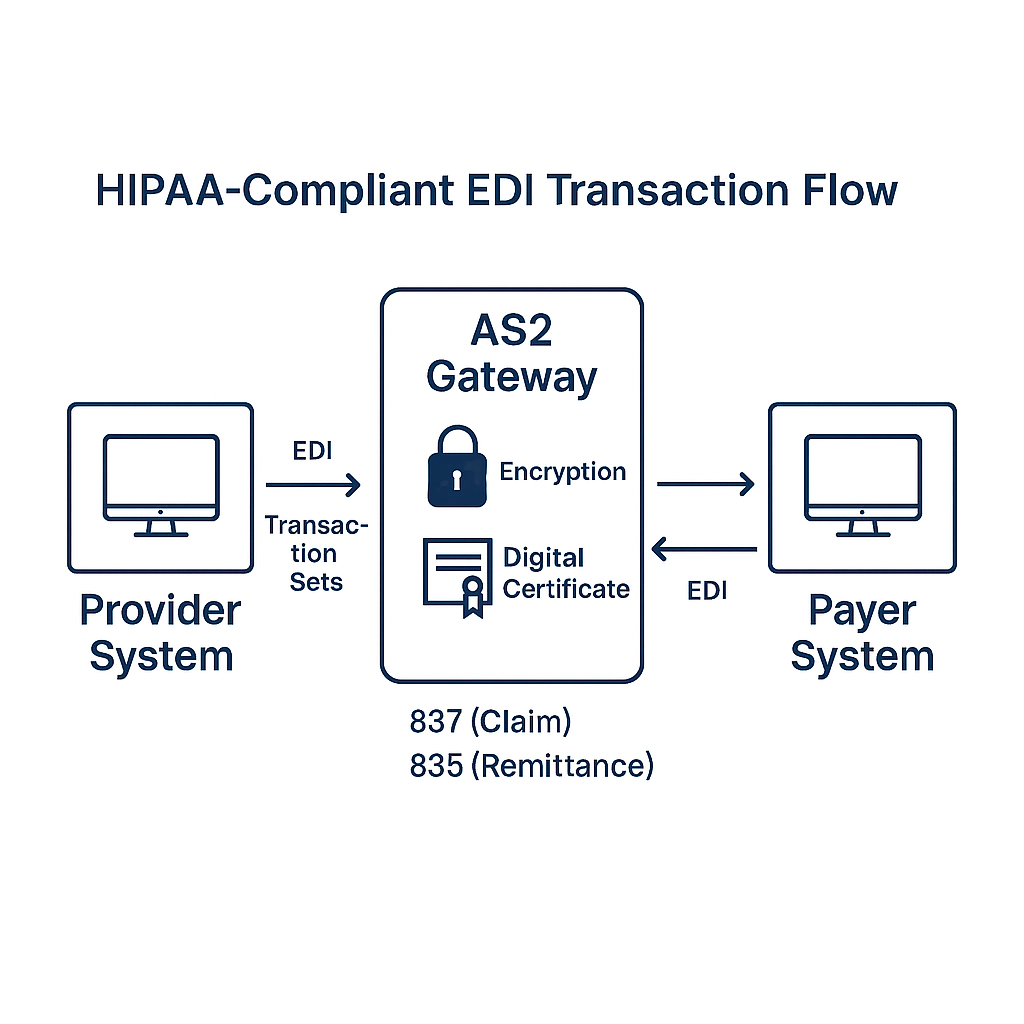
The HIPAA EDI Rule and Adopted Standards
The HIPAA EDI Rule (Part 162 of Title 45 CFR) requires the use of specific transaction and code set standards, notably ASC X12 Version 5010 for EDI transactions and NCPDP for pharmacy data. HHS publishes the adopted standards, which include:
- ASC X12 837: Healthcare Claim (Professional, Institutional, Dental)
- ASC X12 835: Remittance Advice
- ASC X12 270/271: Eligibility Inquiry and Response
- ASC X12 276/277: Claim Status Request and Response
- NCPDP: Electronic Prescription for Drugs (eRx) and Pharmacy Claims (edibasics.com, compliancy-group.com).
Why HIPAA-Compliant EDI Matters
Under HIPAA’s Privacy and Security Rules, any electronic transmission of protected health information (PHI) must implement administrative, physical, and technical safeguards. Non-compliant EDI transmissions risk data breaches, substantial fines (up to $1.5 million per year), and reputational damage. A compliant EDI environment ensures:
- Data Integrity: Transactions are complete and unaltered in transit.
- Confidentiality: EPHI is encrypted during transmission and at rest.
- Authentication: Trading partners are verified via digital certificates or secure credentials.
Common EDI Transaction Sets
One of the most frequently used transaction sets is the ASC X12 837 for claims. It conveys detailed clinical and billing information to payers. The corresponding 835 transaction provides payment and denial explanations. Other critical sets include:
- 270/271 (Eligibility): Verifies a patient’s insurance coverage and benefits before services are rendered (uhcprovider.com, cms.gov).
- 276/277 (Claim Status): Checks the progress and processing status of submitted claims.
- 278 (Prior Authorization): Requests and responds to service authorizations.
- 834 (Enrollment): Manages enrollment and disenrollment in health plans.
Implementing Secure EDI Channels
To safeguard EDI transactions, organizations should employ robust transport protocols—such as SFTP, AS2, or VPN—and enforce TLS 1.2+ encryption. Additionally, digital certificates (X.509) and mutual authentication ensure that data exchanges occur only between verified endpoints.
Managing Trading Partner Agreements
A clear Trading Partner Agreement (TPA) or Business Associate Agreement (BAA) is essential. These contracts define:
- Roles and responsibilities for EDI processing and error resolution.
- Security requirements and incident response procedures.
- Audit and reporting expectations to demonstrate compliance.
EDI Testing and Validation
Before going live, each trading partner must test transaction sets against the chosen EDI platform. Validation steps include:
- Structure and syntax checks against the ASC X12 guide.
- Code set verification for insurance identifiers, diagnosis, and procedure codes.
- End-to-end testing to confirm successful processing and acknowledgments.
Monitoring, Auditing, and Reporting
Continuous monitoring of EDI activity helps detect anomalies—such as unusual transaction volumes or repeated failures. Audit logs should record timestamps, user IDs, and transaction payloads for a minimum of six years per HIPAA’s retention rule (hipaajournal.com).
Common Pitfalls and How to Avoid Them
- Outdated Standards: Failure to upgrade from legacy versions (e.g., 4010) can cause rejections.
- Insufficient Encryption: Using TLS 1.0 or unencrypted FTP exposes PHI to interception.
- Lack of Documentation: Incomplete TPAs or missing audit trails lead to compliance gaps.
Partnering with HIPAA Vault for EDI Solutions
At HIPAA Vault, we offer fully managed, HIPAA-compliant EDI infrastructure. Our solution includes secure AS2 connectors, 24/7 monitoring, certificate management, and a signed BAA—so you can focus on patient care while we handle the complexity of EDI compliance.
Ready to streamline your EDI processes while ensuring HIPAA compliance? Contact us now.